Download: asm.zip
The example assembly program includes examples of arithmetic (add, sub) and logic statements. Values are set using immediate operands.
You can use the Nios II IDE to run or debug assembly programs.
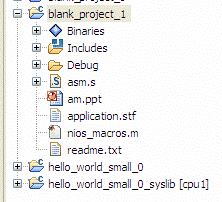
Create a blank project and copy the .s and nios-macros.m
into its directory. The image below shows a portion of the IDE window,
after copying these files.
Select Run -- Debug as ... -- Nios II ISS to debug in the instruction set simulator. Then set the step mode to "single instruction stepping", open up the register window, and start stepping through the code:
This shell script (asm.sh) assembles the source to machine language, runs the disassembler, and runs the instruction-set simulator. result.
You need to change the first line of
asm.s to
.include "./nios_macros.m"
.include "./nios_macros.m"
.text
.global main
.type main, @function
main:
movi r4,2008 # r2 = 2008 (decimal)
movi r5,0x2008 # r3 = 2008 (hex)
movi r4,0x20 # r4 = 20 (hex)
movi r5,0x05 # r5 = 5
add r2,r4,r5 # addition
sub r2,r4,r5 # subtraction
addi r2,r4,3 # immediate addition
/* do some logic operations */
movi r4,0x1100
movi r5,0x1010
and r2,r4,r5
or r2,r4,r5
nor r2,r4,r5
xor r2,r4,r5
andi r2,r4,0x0101
/* do some xor's */
movi r4,2008 # r2 = 2008 (decimal)
movi r5,0x2008 # r3 = 2008 (hex)
xor r4,r4,r5
xor r5,r4,r5
xor r4,r4,r5
end:
br end /* wait here once the program has completed */
.end
#!/bin/sh
name="asm"
nios2-elf-gcc ${name}.s
nios2-elf-size a.out > ${name}.size.txt
nios2-elf-objdump -dS a.out > ${name}.disassemble.txt
nios2-elf-objdump -h a.out > ${name}.headers.txt
nios2-elf-nm a.out > ${name}.symbols.txt
nios2-iss -td:${name}.sim.txt --trace-from=main -f a.out
a.out: file format elf32-littlenios2 Disassembly of section .text: 00000000 <_start>: 0: 06c20034 movhi sp,2048 4: deffc004 addi sp,sp,-256 8: def6303a nor sp,sp,sp c: dec001d4 ori sp,sp,7 10: def6303a nor sp,sp,sp 14: 06800074 movhi gp,1 18: d6a17c04 addi gp,gp,-31248 1c: 06000034 movhi et,0 20: c6018104 addi et,et,1540 24: 00800034 movhi r2,0 28: 10802104 addi r2,r2,132 2c: 1000683a jmp r2 00000030 <main>: 30: 0101f604 movi r4,2008 34: 01480204 movi r5,8200 38: 01000804 movi r4,32 3c: 01400144 movi r5,5 40: 2145883a add r2,r4,r5 44: 2145c83a sub r2,r4,r5 48: 208000c4 addi r2,r4,3 4c: 01044004 movi r4,4352 50: 01440404 movi r5,4112 54: 2144703a and r2,r4,r5 58: 2144b03a or r2,r4,r5 5c: 2144303a nor r2,r4,r5 60: 2144f03a xor r2,r4,r5 64: 2080404c andi r2,r4,257 68: 0101f604 movi r4,2008 6c: 01480204 movi r5,8200 70: 2148f03a xor r4,r4,r5 74: 214af03a xor r5,r4,r5 78: 2148f03a xor r4,r4,r5 0000007c <end>: 7c: 003fff06 br 7c <end>
text data bss dec hex filename
642 896 0 1538 602 a.out
a.out: file format elf32-littlenios2
Sections:
Idx Name Size VMA LMA File off Algn
0 .text 00000280 00000000 00000000 00000074 2**3
CONTENTS, ALLOC, LOAD, READONLY, CODE
1 .rodata 00000002 00000280 00000280 000002f4 2**2
CONTENTS, ALLOC, LOAD, READONLY, DATA
2 .data 0000037c 00000284 00000284 000002f6 2**2
CONTENTS, ALLOC, LOAD, DATA
3 .sdata 00000004 00000600 00000600 00000672 2**2
CONTENTS, ALLOC, LOAD, DATA, SMALL_DATA
4 .sbss 00000000 00000604 00000604 00000676 2**0
CONTENTS, SMALL_DATA
5 .bss 00000000 00000604 00000604 00000676 2**0
ALLOC
6 .comment 00000108 00000000 00000000 00000676 2**0
CONTENTS, READONLY
7 .debug_aranges 000000a0 00000000 00000000 0000077e 2**0
CONTENTS, READONLY, DEBUGGING
8 .debug_pubnames 000000d6 00000000 00000000 0000081e 2**0
CONTENTS, READONLY, DEBUGGING
9 .debug_info 00001499 00000000 00000000 000008f4 2**0
CONTENTS, READONLY, DEBUGGING
10 .debug_abbrev 000004c2 00000000 00000000 00001d8d 2**0
CONTENTS, READONLY, DEBUGGING
11 .debug_line 00000a02 00000000 00000000 0000224f 2**0
CONTENTS, READONLY, DEBUGGING
12 .debug_frame 000000e4 00000000 00000000 00002c54 2**2
CONTENTS, READONLY, DEBUGGING
13 .debug_str 0000068a 00000000 00000000 00002d38 2**0
CONTENTS, READONLY, DEBUGGING
00000604 A __bss_start 00000250 T __fake_fini 00000080 T __fake_init 00000084 T __start_2 00000604 A _edata 00000604 A _end 00000254 T _exit 00000250 W _fini 000085f0 A _gp 00000600 G _impure_ptr 00000080 W _init 00000001 a _nios2_macros_ 00000000 T _start 000000c4 T _zero_bss 0000007c t end 000000d0 T exit 00000284 d impure_data 00000030 T main 000001b4 T memset 07ffff00 A nasys_stack_top
See key for the
meaning of the symbol type characters.
Maintained by John Loomis,
last updated 21 September 2008Simulation
0x00000030 <main>: 0x0101f604 movi r4, 2008 [dstData=0x7d8 dstReg=r4]
0x00000034 <main+0x4>: 0x01480204 movi r5, 8200 [dstData=0x2008 dstReg=r5]
0x00000038 <main+0x8>: 0x01000804 movi r4, 32 [dstData=0x20 dstReg=r4]
0x0000003c <main+0xc>: 0x01400144 movi r5, 5 [dstData=0x5 dstReg=r5]
0x00000040 <main+0x10>: 0x2145883a add r2, r4, r5 [dstData=0x25 dstReg=r2]
0x00000044 <main+0x14>: 0x2145c83a sub r2, r4, r5 [dstData=0x1b dstReg=r2]
0x00000048 <main+0x18>: 0x208000c4 addi r2, r4, 3 [dstData=0x23 dstReg=r2]
0x0000004c <main+0x1c>: 0x01044004 movi r4, 4352 [dstData=0x1100 dstReg=r4]
0x00000050 <main+0x20>: 0x01440404 movi r5, 4112 [dstData=0x1010 dstReg=r5]
0x00000054 <main+0x24>: 0x2144703a and r2, r4, r5 [dstData=0x1000 dstReg=r2]
0x00000058 <main+0x28>: 0x2144b03a or r2, r4, r5 [dstData=0x1110 dstReg=r2]
0x0000005c <main+0x2c>: 0x2144303a nor r2, r4, r5 [dstData=0xffffeeef dstReg=r2]
0x00000060 <main+0x30>: 0x2144f03a xor r2, r4, r5 [dstData=0x110 dstReg=r2]
0x00000064 <main+0x34>: 0x2080404c andi r2, r4, 257 [dstData=0x100 dstReg=r2]
0x00000068 <main+0x38>: 0x0101f604 movi r4, 2008 [dstData=0x7d8 dstReg=r4]
0x0000006c <main+0x3c>: 0x01480204 movi r5, 8200 [dstData=0x2008 dstReg=r5]
0x00000070 <main+0x40>: 0x2148f03a xor r4, r4, r5 [dstData=0x27d0 dstReg=r4]
0x00000074 <main+0x44>: 0x214af03a xor r5, r4, r5 [dstData=0x7d8 dstReg=r5]
0x00000078 <main+0x48>: 0x2148f03a xor r4, r4, r5 [dstData=0x2008 dstReg=r4]
0x0000007c <end>: 0x003fff06 br 0x7c <end>